Google-OIDC Integration Guide
Operational Scenarios
Google Cloud's OIDC-based Single Sign-On (SSO) provides a secure authentication method that allows users to access multiple services with a single identity.
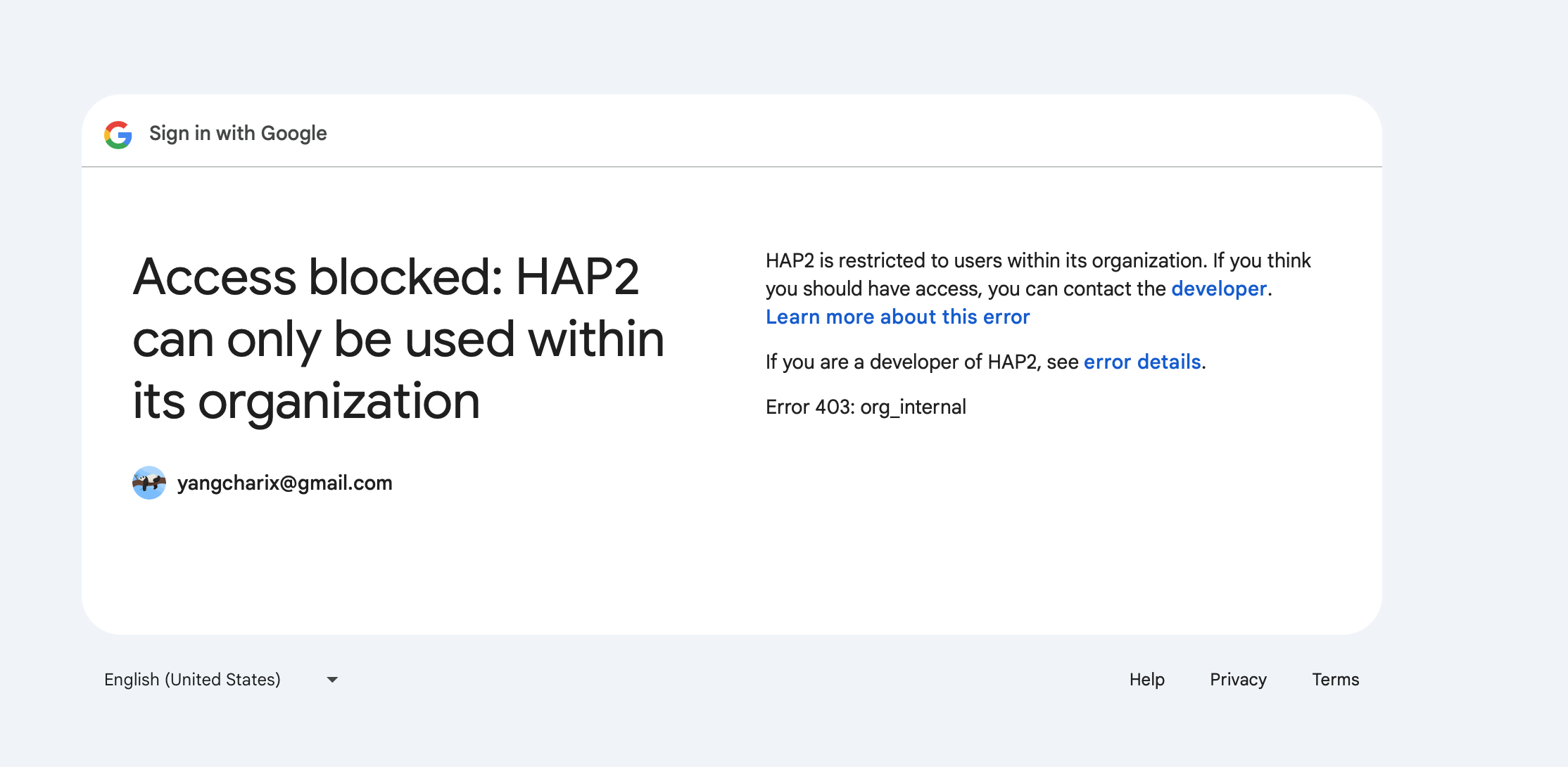
Google OIDC supports both internal and external user access control (if not a Google Workspace user, the application can only be provided to external users).
Prerequisites
- Have a Google account
Operation Steps
Configure OAuth2.0 Client Application
-
Log in to Google Cloud Console
-
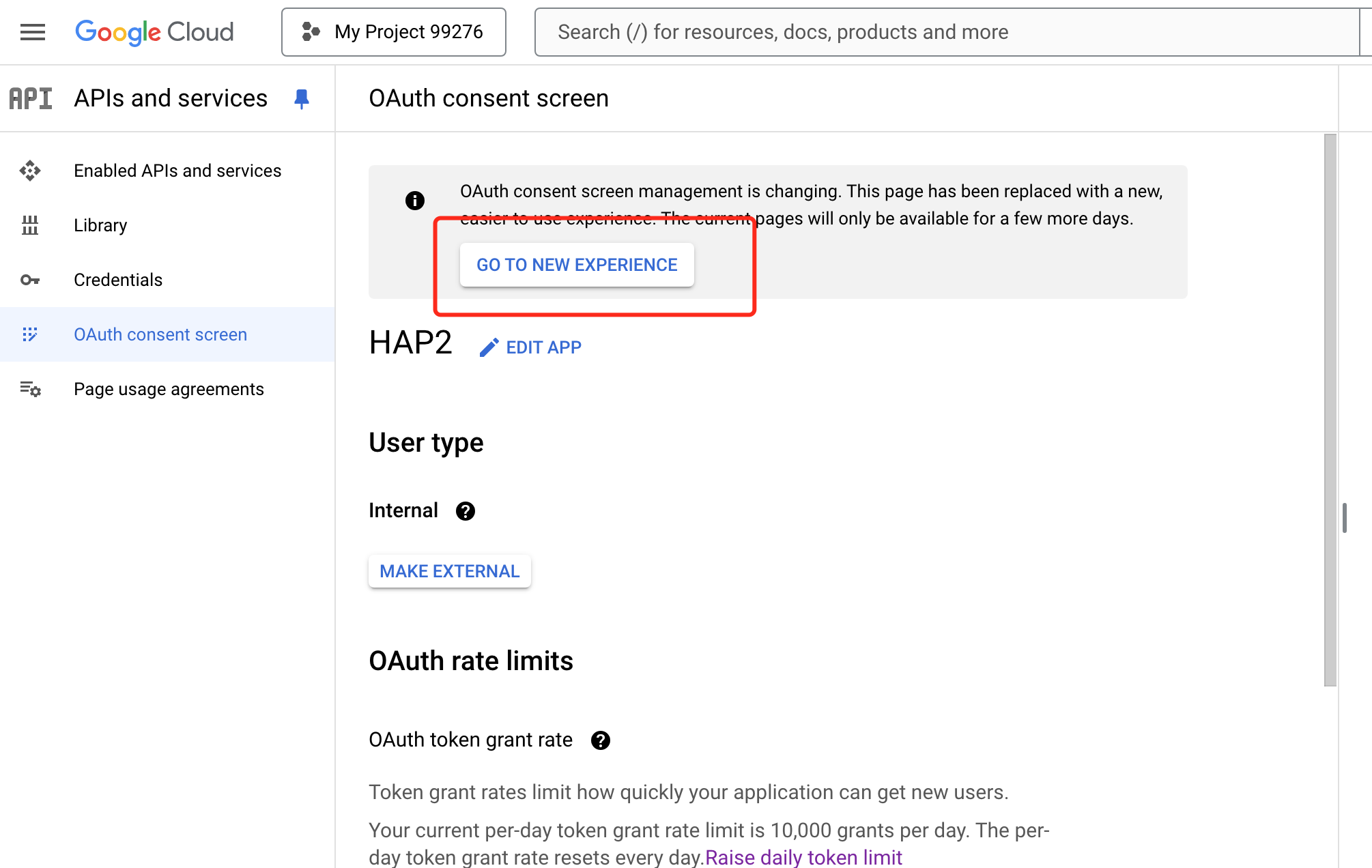
Access security settings; navigate to APIs & Services > OAuth consent screen.
-
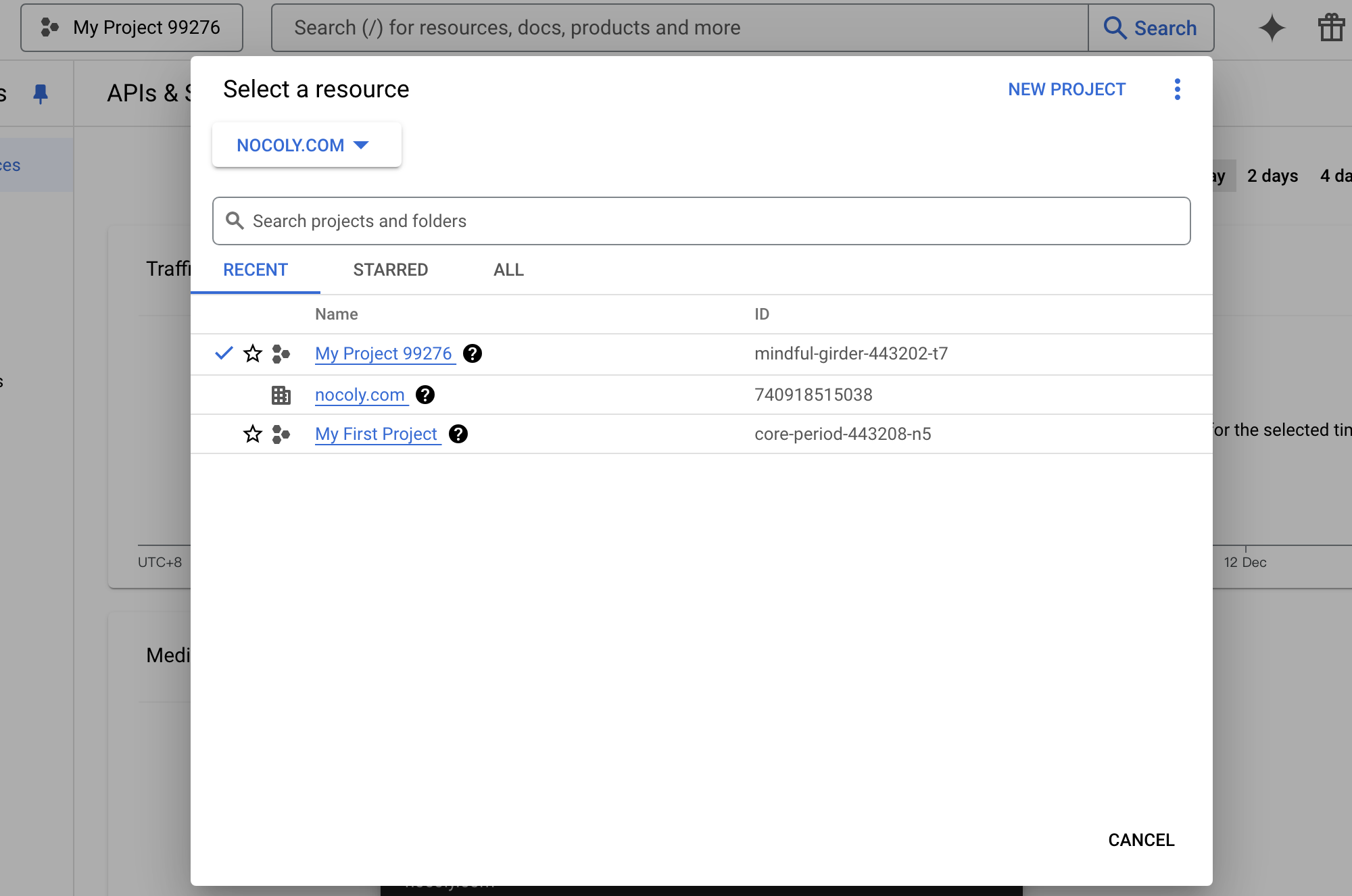
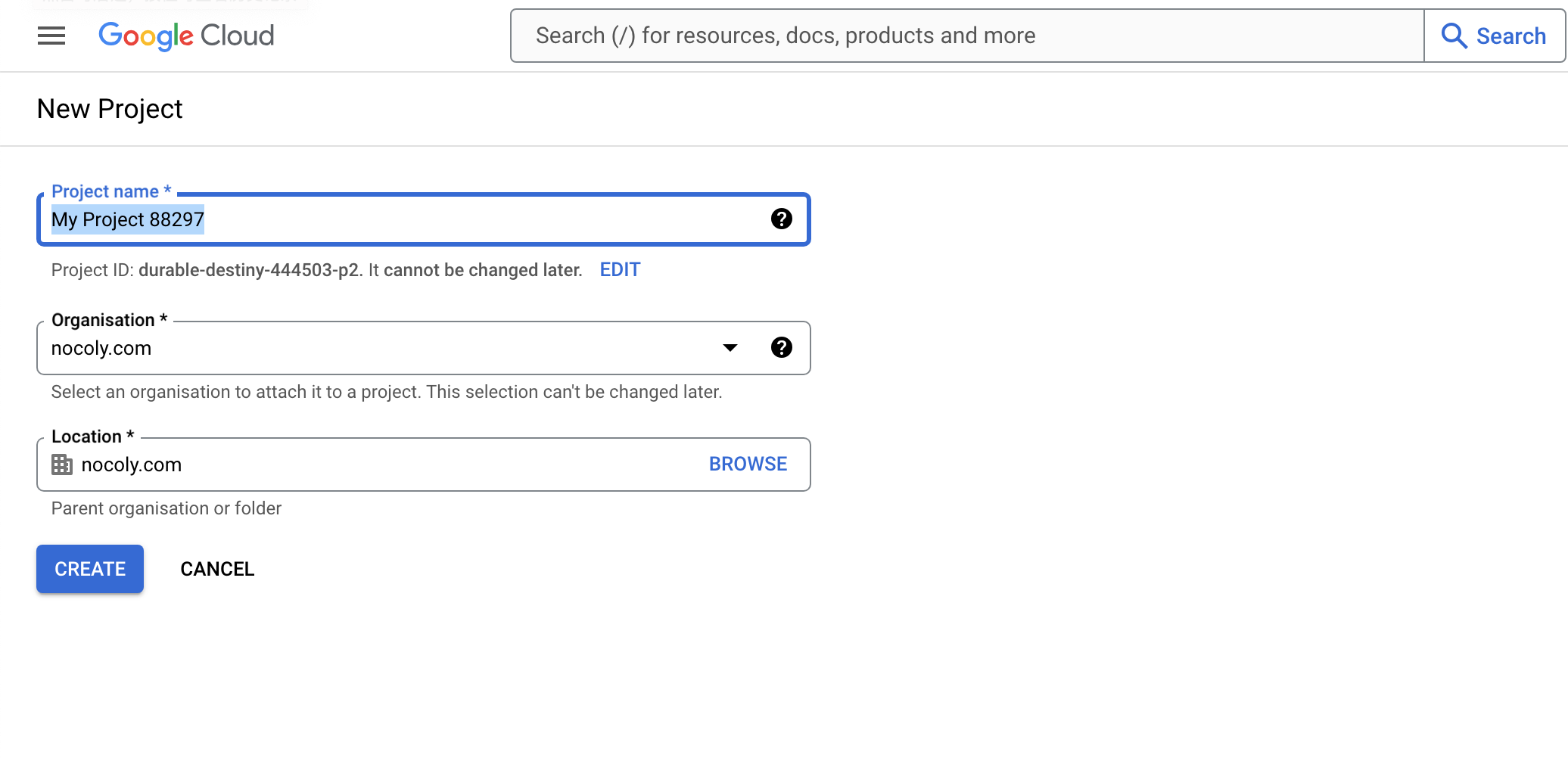
Choose to create a project or use an existing project
-
Create an application under the project,Fill in the branding and audience informatio
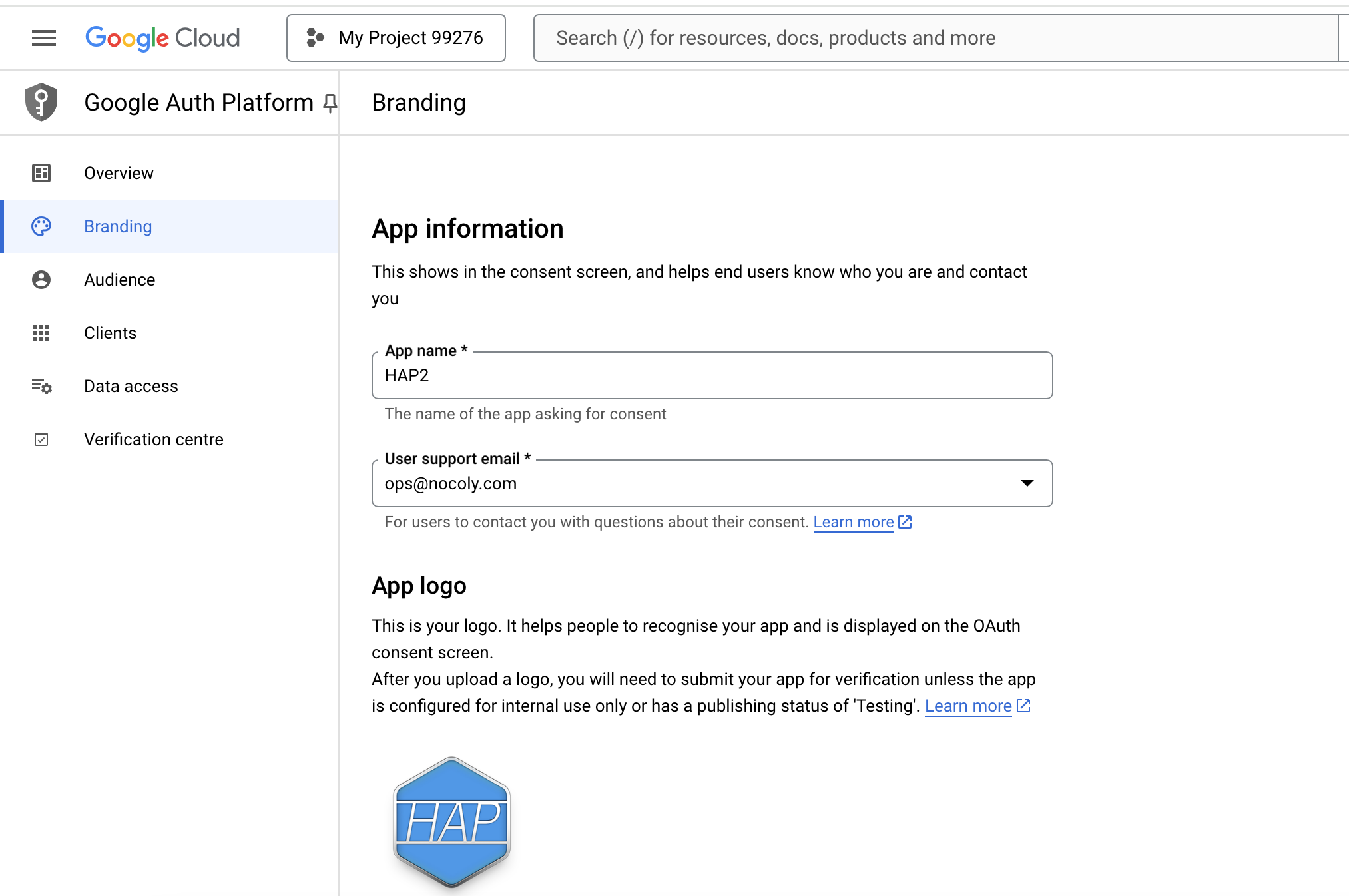
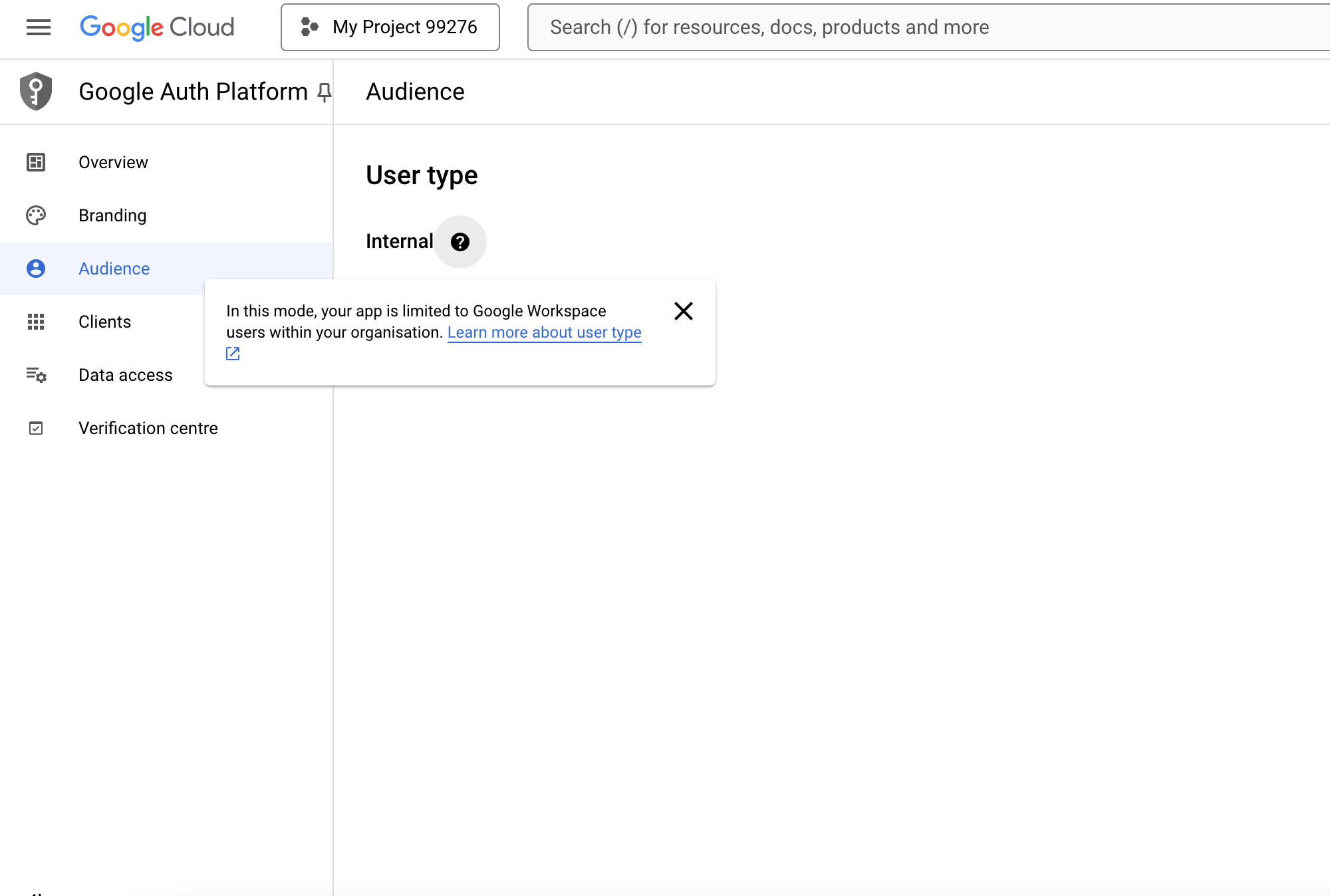
-
Create an
OAuth2.0client,Configure redirect address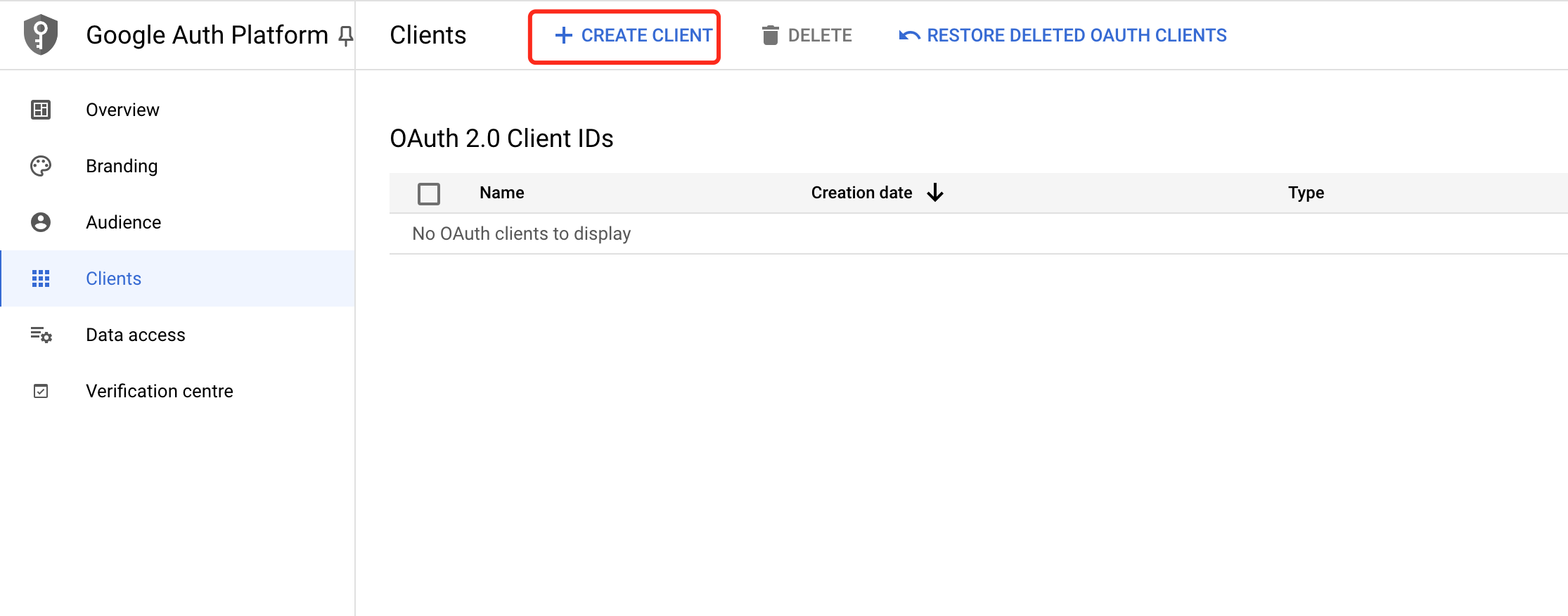
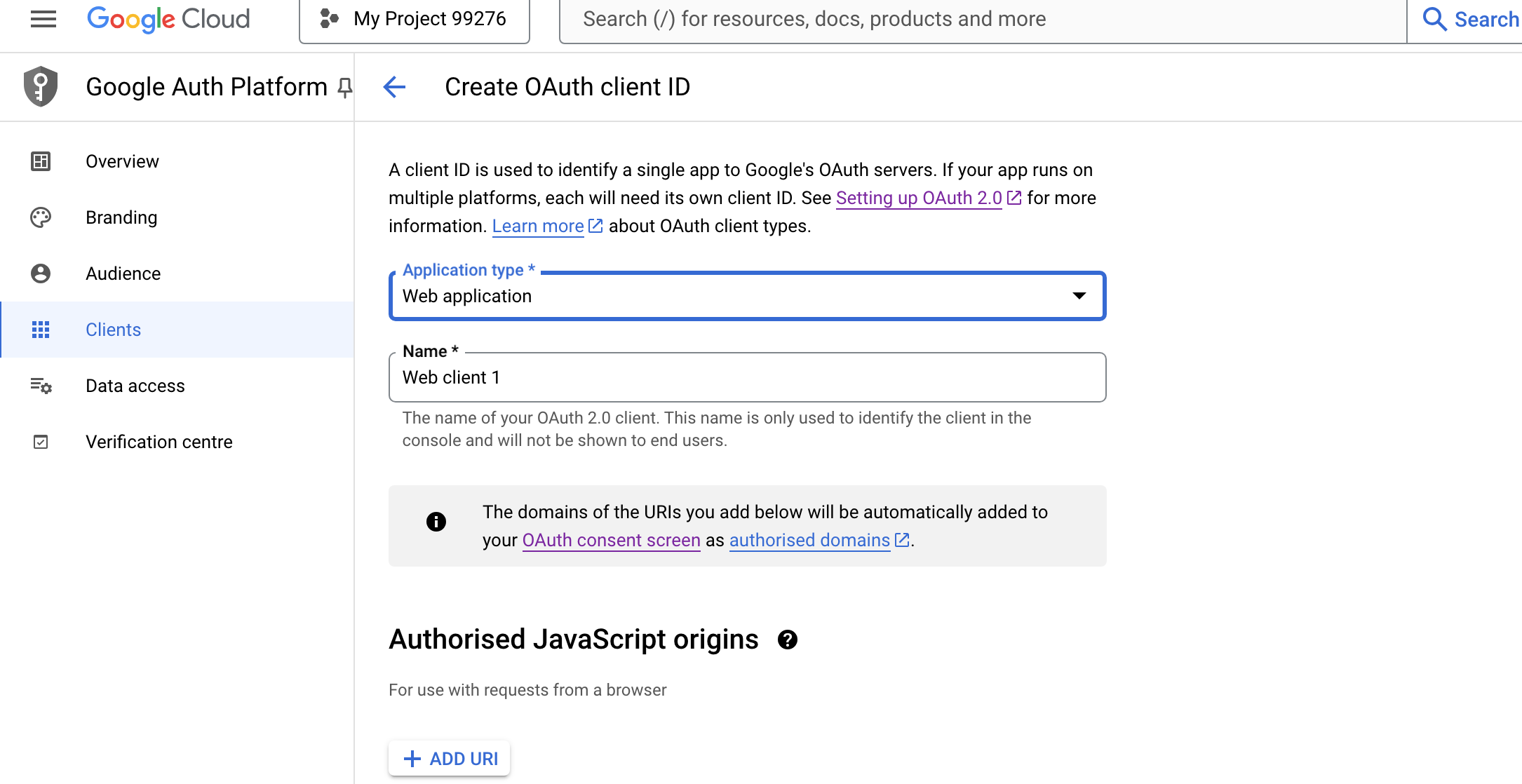
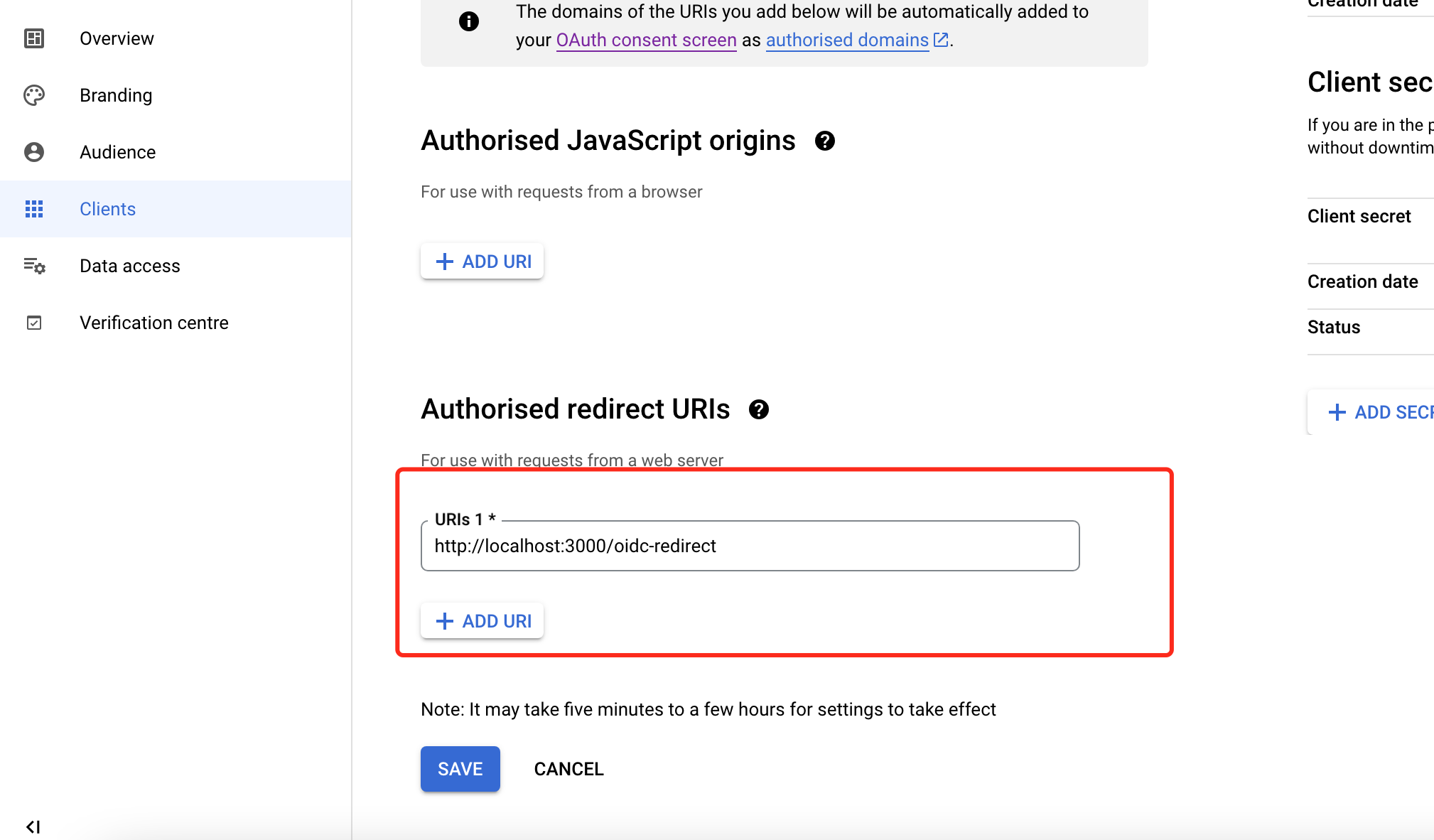
-
After creation, download the
OIDCrelated configuration for laterHAPconfiguration ofOIDCSingle Sign-On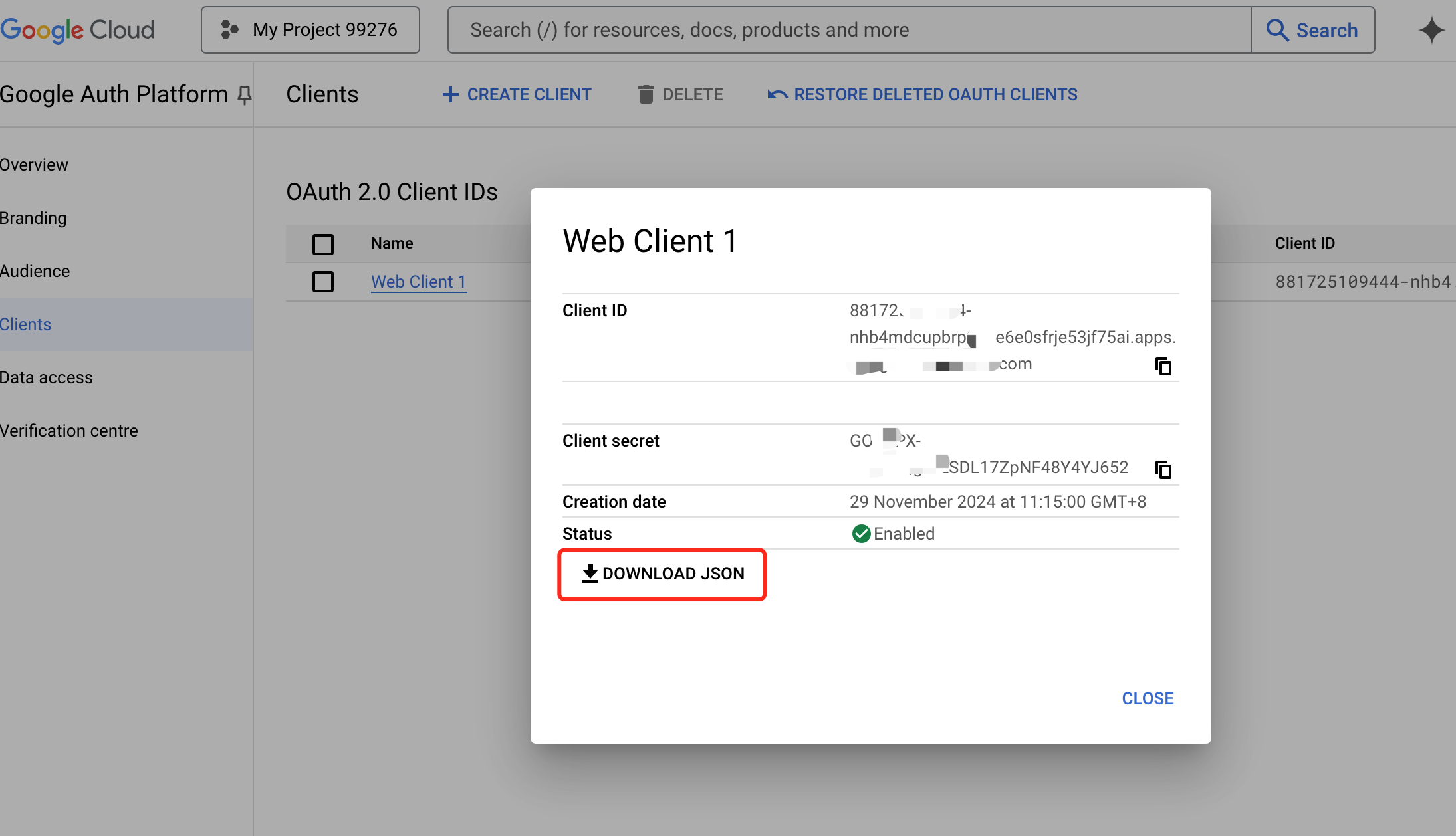
HAP Integration with OIDC Single Sign-On
For detailed steps, refer to the HAP private deployment documentation How to Integrate Single Sign-On - OIDC.
-
Configure
sso.json, content as follows: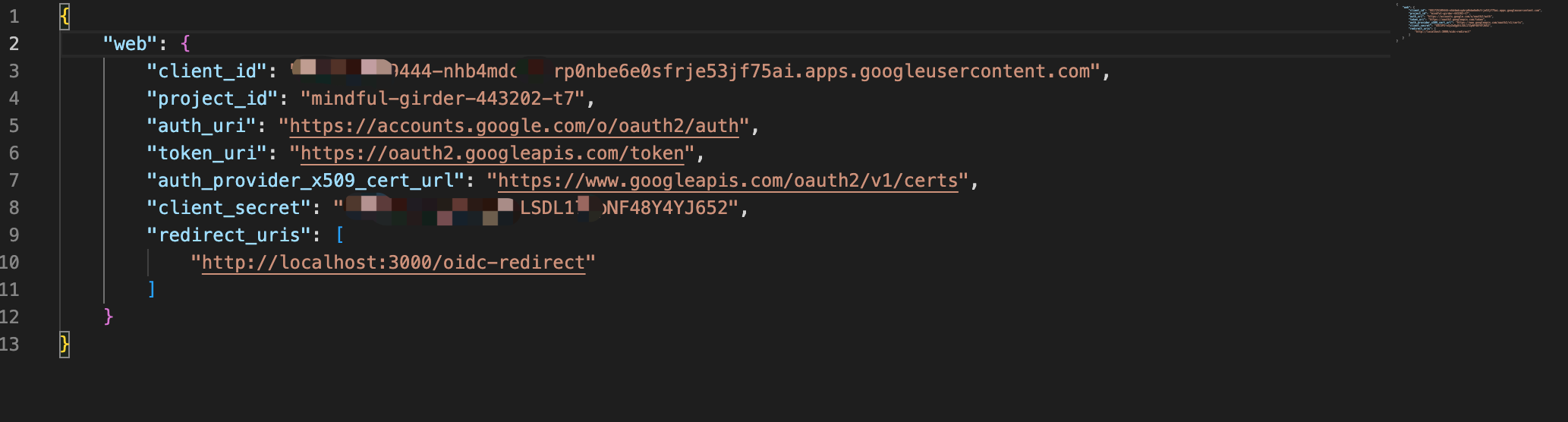
{
"mode": "common-oidc",
"name": "oidc",
"oidc": {
"clientId": "x-x.apps.googleusxx",
"clientSecret": "x-xxxyZwQgUtLSDL17Zpxxx",
"oidcUrl": "https://accounts.google.com/.well-known/openid-configuration",
"redirectUrl": "http://localhost:3000/oidc-redirect",
"responseTypes": "code",
"scope": "openid email profile",
"params": {
"UserId": "sub",
"Name": "name",
"Email": "email"
},
"autoRegister": true,
"projectId": ""
}
} -
Mount the
OIDCconfiguration file (as follows), then restart the service.- ./volume/sso/sso.json:/usr/local/MDPrivateDeployment/sso/OptionFile/sso.json -
Restart completed.
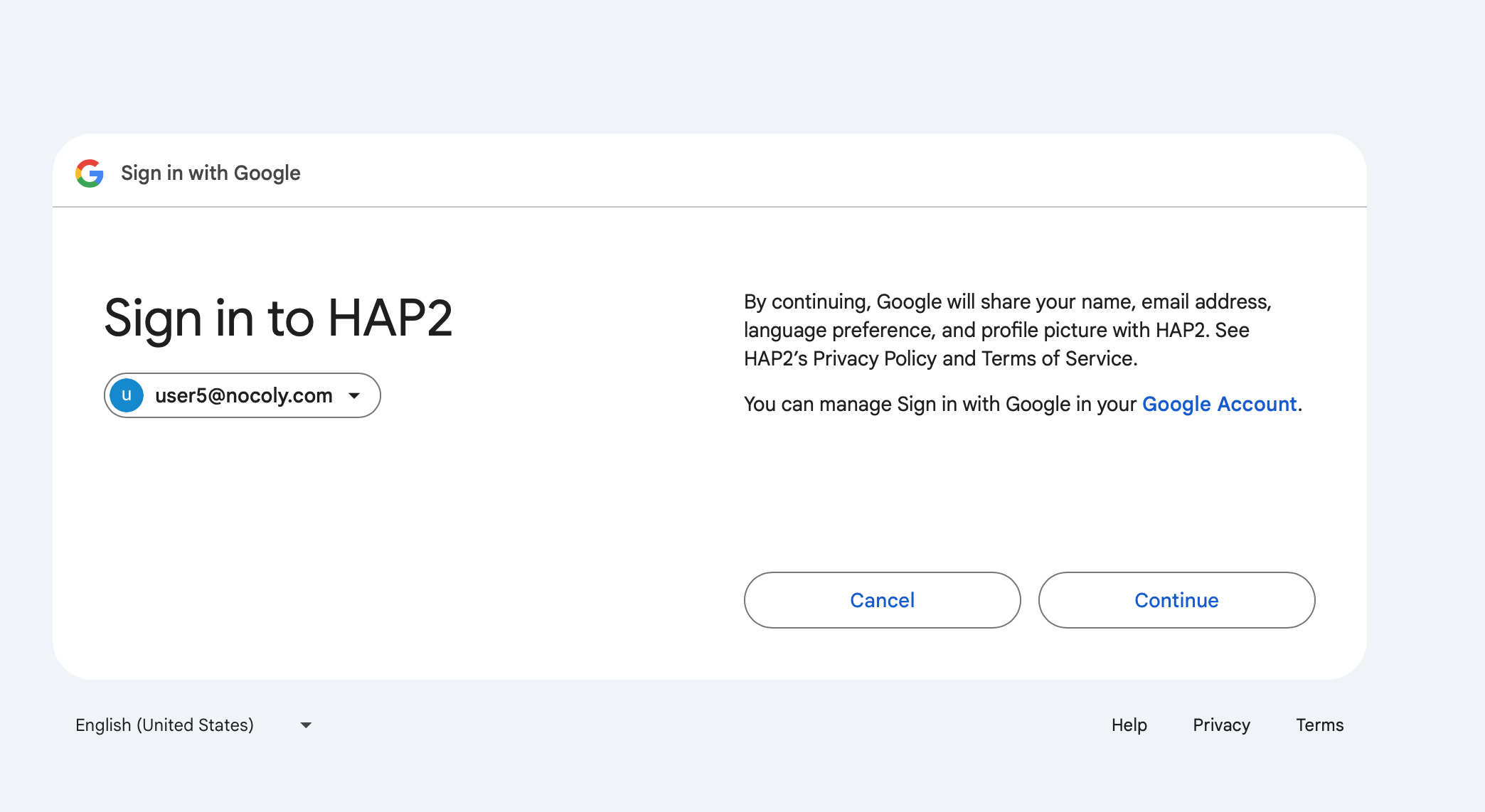
User SSO Login
-
Enter
{HAP}/orgsso/oidcor{HAP}/orgsso/ssoin the browser to log in. -
Log in to the organizational account and authorize.
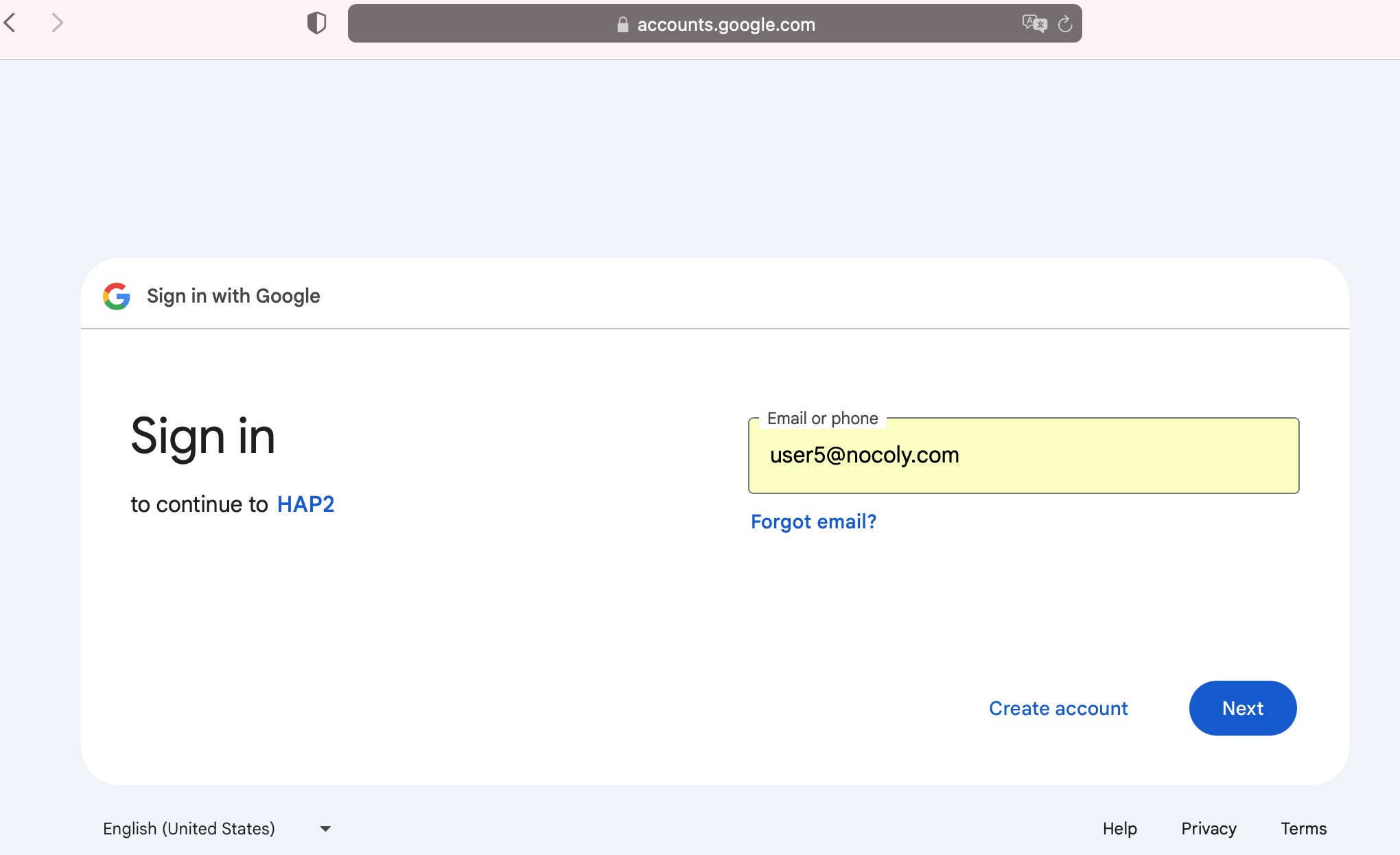
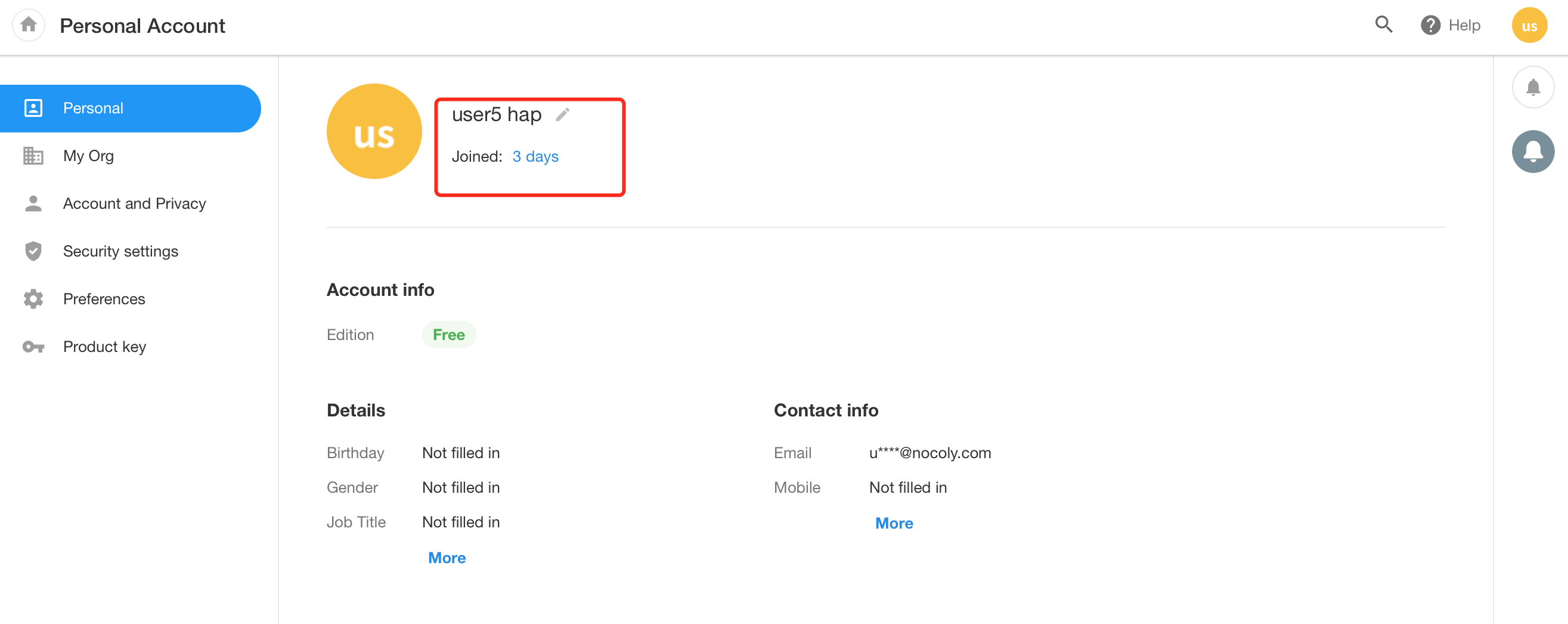
-
Switch to an external user.
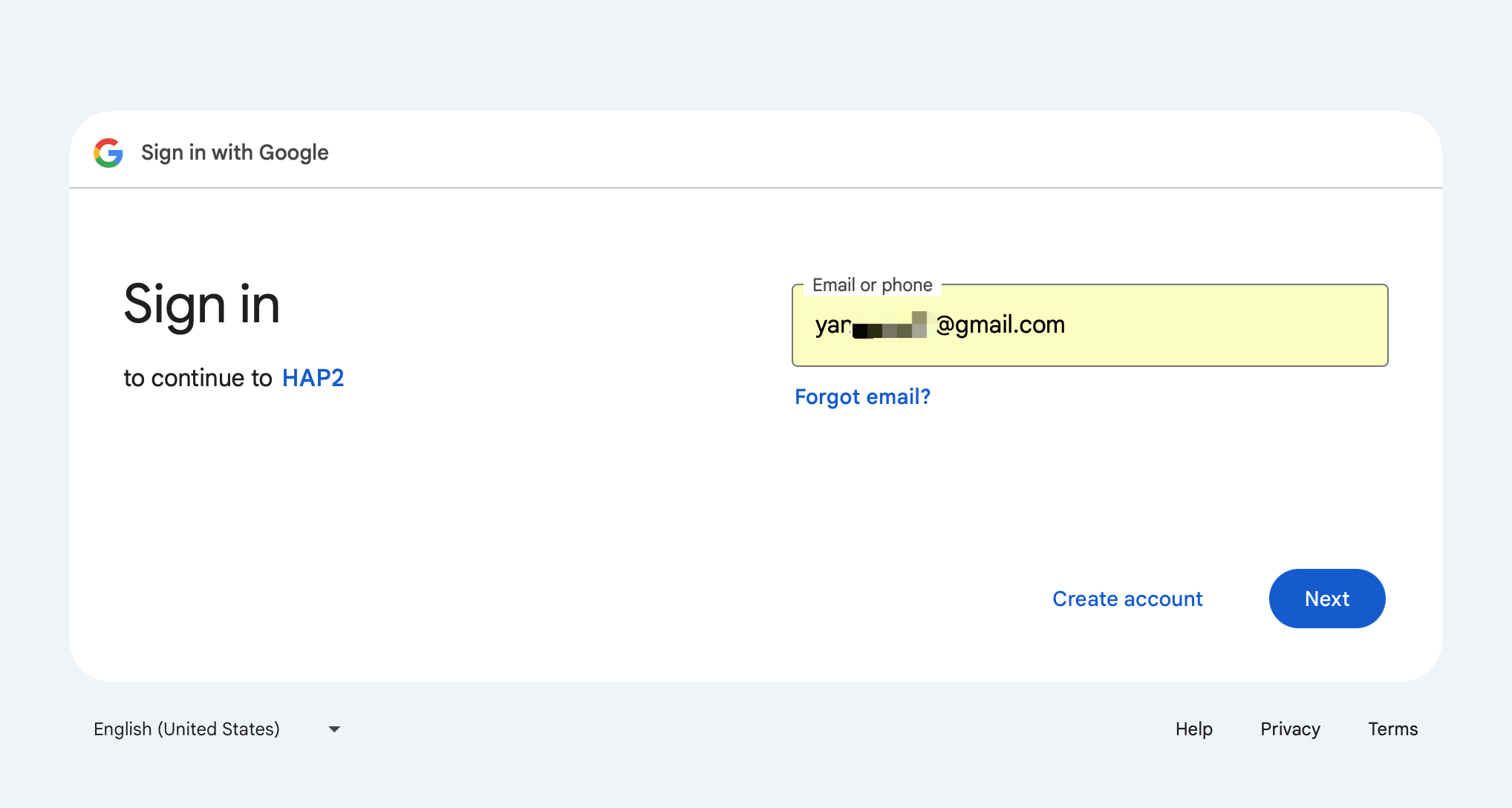
-
Access is prohibited.